مزود حلول التكنولوجيا لم يعد رفاهية—إنه ضروري لنجاح الأعمال في المملكة العربية السعودية.

A technology solutions provider is no longer a luxury—it’s essential for business success in Saudi Arabia. Whether you’re a growing enterprise in Riyadh or an established organization across the Kingdom, selecting the right technology solutions provider determines your competitive advantage, operational efficiency, and security posture.
This comprehensive guide explores how modern tech solutions transform businesses, what IT service provider options exist, and how to identify the best top IT solutions provider Saudi Arabia has to offer.
What is a Technology Solutions Provider and Why Your Business Needs One
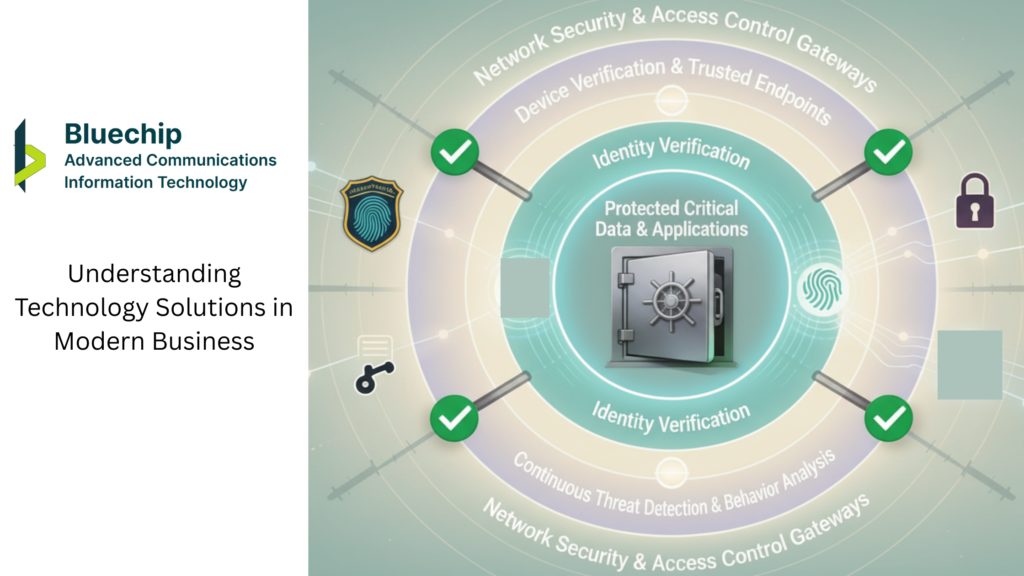
Understanding Technology Solutions in Modern Business
A technology solutions provider offers comprehensive business technology services designed to solve organizational challenges, enhance operations, and enable digital transformation. Unlike generic IT departments, a professional technology solutions provider brings specialized expertise across multiple domains:
Infrastructure Management – Servers, networks, cloud platforms
Cybersecurity & Network Security – Protection against evolving threats
Identity and Access Management – Secure credential management
Cloud Solutions – Scalable infrastructure for growth
Data Loss Protection – Safeguarding critical business information
Patch Management – Continuous system security updates
Custom IT Software Solutions – Tailored applications for unique needs
The best top IT solutions provider in Saudi Arabia understands regional regulatory requirements, Vision 2030 compliance needs, and the specific business landscape of the Kingdom.
مزود حلول التكنولوجيا يقدم خدمات شاملة لحل التكنولوجيا مصممة لحل التحديات التنظيمية.
إن أفضل مزود لحلول تكنولوجيا المعلومات في المملكة العربية السعودية يفهم المتطلبات التنظيمية الإقليمية، واحتياجات الامتثال لرؤية 2030، والبيئة التجارية الخاصة بالمملكة.Why Businesses in Saudi Arabia Choose Professional Technology Solutions Providers
IT service provider options have multiplied significantly. Organizations now choose dedicated technology solutions provider partnerships because:
Expertise at Scale – Access to specialists in every technology domain
24/7 Operational Support – Continuous monitoring prevents costly downtime
Security Compliance – Meet NCA, CITC, and Vision 2030 requirements
Cost Optimization – Reduce overhead through managed services
Strategic Growth – Technology that scales with your business
Risk Mitigation – Advanced cyber security and vulnerability management
Business Continuity – Disaster recovery and backup systems
Businesses utilizing managed IT services report 30-40% improvements in operational efficiency and significant reductions in security incidents.
Core IT Services and Technology Solutions Offered by Leading Providers
Comprehensive IT Service Provider Options Available
When evaluating IT service provider options, understand the breadth of services modern technology firms offer:
Cloud Solutions Riyadh and Across the Kingdom

Cloud solutions Riyadh providers enable businesses to move from traditional on-premises infrastructure to flexible, scalable cloud environments. This includes:
Multi-Cloud Architecture – Leverage multiple cloud providers (AWS, Azure, Google Cloud)
Hybrid Cloud Integration – Blend cloud and on-premises resources
Cloud Migration Services – Seamless transition with minimal disruption
Cloud Security Management – Protecting assets in cloud environments
Cost Optimization – Reducing cloud spending through intelligent management
Cloud solutions are critical for Vision 2030 compliance and support the Kingdom’s digital transformation goals.
حلول سحابية الرياض تمكّن الشركات من الانتقال من البنية الأساسية التقليدية
Cybersecurity and Network Security Solutions
Cyber security and network security form the foundation of modern IT operations. Leading providers offer:
Zero Trust Security Architecture – Never trust, always verify approach
Advanced Threat Detection – AI-powered threat identification
Incident Response – Rapid containment of security breaches
Security Operations Center (SOC) – 24/7 threat monitoring
Penetration Testing – Identify vulnerabilities before attackers do
Cyber Security companies specializing in your industry vertical
Organizations utilizing comprehensive cyber security services reduce breach risk by up to 80%.
الأمن السيبراني وأمن الشبكات يشكلان أساس العمليات الحديثة
Identity and Access Management Solutions
Identity and access management controls who accesses what resources—critical for security and compliance:
Multi-Factor Authentication – Enhanced login security
Privileged Access Management – Secure credential vaulting
Role-Based Access Control – Granular permission management
Identity Governance – Continuous access reviews and compliance
Single Sign-On – Simplified user experience with security
Privileged access management is particularly important for protecting administrative accounts and sensitive systems.
حلول إدارة الهوية والوصول تتحكم في من يمكنه الوصول إلى موارد المؤسسة
Patch Management and Vulnerability Management
Continuous security requires systematic patch management and vulnerability management:
Automated Patch Deployment – Updates applied systematically
Vulnerability Scanning – Regular security assessments
Threat Intelligence – Stay informed on emerging threats
Configuration Management – Secure system baselines
Compliance Scanning – Verify regulatory compliance
Unpatched systems account for 60% of successful cyber attacks. Modern patch management reduces this risk dramatically.
إدارة الثغرات الأمنية وإدارة الرقع تتطلب نهجاً منتظماً
Data Protection and Data Loss Prevention
Protecting sensitive business information is paramount:
Data Loss Prevention (DLP) – Prevent unauthorized data exfiltration
Data Security – Encryption and secure storage
Data Protection – Compliance with regulations like GDPR equivalents
Backup and Recovery – Automated daily backups with rapid restoration
Information Security – Comprehensive data governance
Data loss protection prevents costly breaches and regulatory violations.
حماية البيانات ومنع فقدان البيانات أمر بالغ الأهمية
Web Application Security
Modern businesses depend on web applications—securing them is critical:
Web Application Firewalls – Block malicious traffic
Application Security Testing – Find vulnerabilities before deployment
API Security – Protect data exchange between applications
Secure Development – Build security into development process
Runtime Protection – Monitor applications in production
Web application vulnerabilities expose customer data and business logic.
IT Solution Benefits Explained – Real-World Impact
IT Solution Benefits Explained – Real-World Impact
Organizations partnering with top IT solutions provider Saudi Arabia firms experience tangible improvements:
Increased Uptime and Business Continuity
Benefits of managed IT:
99.9% uptime guarantees (vs. 95% typical in-house)
Rapid incident response (under 4 hours)
Proactive monitoring prevents failures
Disaster recovery ensures business continuity
Reduced loss from downtime
IT solutions for business that prioritize availability directly impact revenue preservation.
Enhanced Security and Compliance
Professional IT service provider options implement enterprise-grade security:
Reduced breach risk by 70-80%
Compliance with NCA, CITC requirements
Continuous security monitoring
Regulatory reporting capabilities
Executive dashboards showing security posture
Enhanced Security and Compliance
Custom IT software solutions and managed services optimize budgets:
Predictable monthly costs (vs. surprise repairs)
Reduced emergency expenses
Optimized cloud spending
Elimination of unnecessary software licenses
Strategic technology investments aligned with business goals
Improved Employee Productivity
Modern IT solutions for business enable productivity:
Faster system performance
Seamless cloud access from anywhere
Simplified user experience
Modern collaboration tools
Reduced waiting time for IT support
IT Outsourcing Sector Growth and Market Trends in Saudi Arabia
The Evolution of IT Service Provider Options
The IT outsourcing sector growth in Saudi Arabia reflects the Kingdom’s digital transformation commitment:
Market Expansion – Growing number of Saudi IT consulting firms and specialized providers
Service Specialization – Providers focusing on specific industries (banking, healthcare, retail)
Technology Innovation – Adoption of AI, IoT, and advanced automation
Local Expertise – Saudi Arabia IT company providers understanding regional context
Vision 2030 Alignment – Technology solutions supporting national goals
Saudi IT consulting firms are increasingly valued for their understanding of local regulatory environment and business practices.
Key Trends Shaping IT Solutions in Saudi Arabia
Zero Trust Security Architecture
Zero trust represents a fundamental shift from “trust but verify” to “never trust, always verify”:
Every access request authenticated and authorized
Continuous monitoring and validation
Significantly reduces breach impact
Becomes standard across enterprises
Cyber security companies now offer zero trust implementations
Zero Trust Security Architecture
Innovative technology solutions increasingly incorporate AI:
Automated threat detection
Intelligent patch management
Predictive maintenance
AI-powered security analysis
Automated compliance reporting
Zero Trust Security Architecture
Cloud solutions have become primary infrastructure:
Cloud solutions Riyadh becoming standard deployment option
Migration from legacy on-premises systems
Hybrid cloud architectures for flexibility
Cloud-native application development
Cost advantages driving adoption
Zero Trust Security Architecture
With cybersecurity talent in short supply, organizations turn to:
Security companies offering managed security services
24/7 SOC monitoring from experts
Specialized threat intelligence
Incident response retainers
Training and awareness programs
Best IT Solutions Saudi Arabia – Evaluating Your Options
What Makes a Best IT Solutions Saudi Arabia Provider
When searching for best IT solutions Saudi Arabia options, evaluate:
Comprehensive Service Portfolio
Leading Saudi Arabia IT company providers offer:
Full spectrum of technology solutions (not just one or two services)
Integration across services (security, infrastructure, applications)
Customization to your specific needs
Scalability as your organization grows
Local Expertise and Regional Compliance
Top IT solutions provider Saudi Arabia firms understand:
NCA (National Cybersecurity Authority) requirements
CITC (Communications and Information Technology Commission) regulations
Vision 2030 compliance needs
Local business practices and culture
Regional security threats
Proven Track Record
Evaluate IT consulting firms based on:
Number of successful implementations
Industry experience (banking, healthcare, government, etc.)
Client retention rates
Case studies and testimonials
Awards and certifications
24/7 Support and Responsiveness
Professional IT service provider options guarantee:
24/7/365 technical support
Response time commitments
Dedicated account management
Proactive monitoring
Regular business reviews
Innovation and Forward Thinking
Choose providers demonstrating:
Investment in emerging technologies
Continuous team training and certification
Participation in industry groups
Thought leadership content
Commitment to client success
Key Questions to Ask Technology Solutions Providers
When evaluating technology solutions provider options:
Service Delivery: How do you deliver services? On-premises, cloud, hybrid?
Security: What cyber security certifications do your team hold?
Experience: How many organizations like mine do you support?
Technology: What platforms and tools do you specialize in?
Support: What’s your response time commitment?
Compliance: Can you help with NCA and regulatory requirements?
Growth: How do you support business scaling?
Innovation: How do you help us stay current with emerging threats?
Custom IT Software Solutions – Tailored Technology for Your Business
Beyond Off-the-Shelf Solutions
Many organizations require more than standard software—they need custom IT software solutions:
When to Consider Custom Development
Organizations choose custom IT software solutions when:
Off-the-shelf tools don’t match workflows
Integration between systems is complex
Competitive advantage requires proprietary solutions
Legacy system modernization is needed
Unique business processes require automation
Benefits of Custom IT Software Solutions
Custom IT software solutions provide:
Perfect fit to business requirements
Integration with existing systems
Competitive differentiation
Better user adoption (aligned with workflows)
Long-term cost advantages
Ownership of intellectual property
Development and Implementation Process
Professional providers managing custom IT software solutions:
Conduct thorough requirements analysis
Design scalable, secure architectures
Follow secure development practices
Implement modern development methodologies (Agile, DevOps)
Provide comprehensive training and documentation
Support ongoing maintenance and updates
IT Solutions for Business – Transforming Organizational Performance
Industry-Specific Technology Solutions
Different industries require specialized IT solutions for business:
Banking and Financial Services
Compliance with financial regulations
Transaction security and fraud prevention
Customer data protection
High availability systems
Advanced encryption for sensitive data
Healthcare Organizations
Patient data privacy (healthcare equivalent of GDPR)
Secure communication systems
Backup and disaster recovery
Telemedicine infrastructure
Electronic health record systems
Retail and E-Commerce
Payment processing security
Customer data management
Inventory systems integration
Online store infrastructure
Sales analytics and reporting
Government and Public Sector
Compliance with public sector standards
High-security infrastructure
Citizen data protection
Efficient service delivery
Transparency and audit capabilities
Manufacturing and Industrial
Operational technology (OT) security
Production system monitoring
Supply chain integration
Predictive maintenance
Quality control systems
Benefits of Managed IT Services – Comprehensive Guide
Understanding Managed IT Services Model
Benefits of managed IT services extend beyond just technical support:
Predictable Cost Structure
Monthly service costs (vs. surprise expensive repairs)
Budget planning becomes precise
No capital expenditure for equipment
Staffing costs eliminated
Transparent pricing models
Access to Expert Talent
Team of specialists across technologies
Advanced certifications and training
Industry best practices implementation
Problem-solving expertise
Continuous professional development
Proactive Maintenance and Monitoring
24/7 system monitoring prevents problems
Scheduled maintenance during low-use periods
Patch management handled automatically
Performance optimization ongoing
Security threat detection real-time
Scalability and Flexibility
Add or remove services as needs change
Support business growth without infrastructure burden
Flexibility to adopt new technologies
Right-sizing of resources
No overprovisioning of capacity
Focus on Core Business
IT management outsourced to experts
Leadership focuses on strategic goals
Reduced operational complexity
Faster time to market for new initiatives
Competitive advantage through technology
The Future of Technology Solutions and What It Means for Your Business
Emerging Technologies Reshaping the Landscape
The future of technology solutions includes:
Artificial Intelligence Integration
AI is transforming security and operations:
Automated threat detection with AI
Predictive analytics for maintenance
Natural language processing for queries
Machine learning for anomaly detection
Intelligent resource optimization
Artificial Intelligence Integration
Distributed computing brings processing closer to data:
Real-time data processing
Reduced latency for applications
Enhanced privacy through local processing
Scalable IoT solutions
Industrial automation
Artificial Intelligence Integration
Quantum computing will break current encryption:
Organizations preparing cryptographic migration
Post-quantum cryptography implementation
Long-term security strategy planning
Regulatory requirements evolving
Artificial Intelligence Integration
Environmental responsibility becoming mainstream:
Energy-efficient data centers
Cloud consolidation reducing footprint
Green technology adoption
Corporate sustainability goals
Regulatory environmental compliance
Conclusion – Choosing Your Technology Solutions Partner
Selecting a technology solutions provider is among the most important technology decisions your organization will make. The right partner—whether you’re seeking IT solutions for business transformation, managed IT support, or custom IT software solutions—becomes an extension of your team and critical partner in achieving business goals.
Look for providers offering comprehensive technology solutions, proven expertise, strong security practices, and genuine partnership approach. Your success depends on it.
اختيار مزود حلول التكنولوجيا هو من أهم القرارات التكنولوجية التي ستتخذها مؤسستك.
